An internal order is a tool within cost accounting used to monitor costs and, in some cases, revenues associated with specific tasks, projects, or activities within an organization. It provides a means for detailed tracking of financial transactions, enabling businesses to plan, monitor, and allocate costs effectively. These types of orders, generated via internal ordering systems, are versatile and can be used for various purposes, including tracking overhead costs, investment costs, accrual calculations, and even costs and revenues for specific activities that do not directly impact the core business operations. Investing in the right custom order management software is vital to ensuring seamless administration and optimization of these orders within organizations.
Why an Internal Order is Required
These orders are crucial for maintaining and enhancing financial transparency and control within an organization. Here’s why they are required:
- Facilitate Detailed Cost Tracking: They allow for the detailed tracking of costs tied to specific activities, aiding in improved budget management and financial planning.
- Segregate Costs: By segregating costs on a per-project or per-activity basis, internal orders help organizations identify where funds are being spent and uncover areas of inefficiency.
- Implement Cost-Saving Measures: The insights gained from these orders enable organizations to identify and implement cost-saving measures effectively.
- Support Accurate Cost Allocation: They ensure that expenses are accurately allocated to the correct department, project, or activity, facilitating a fair and precise financial evaluation.
- Aid in Profitability and Performance Evaluation: The precise allocation of costs helps in evaluating the profitability and financial performance of various organizational segments.
- Comply with Reporting and Auditing Requirements: Internal orders generated through internal ordering systems are instrumental in fulfilling financial reporting and auditing standards by providing a clear audit trail of transactions.
- Empower Strategic Decision Making: With enhanced financial transparency, organizations can make informed strategic decisions, optimizing resource allocation and overall financial management.
Different Types of Internal Orders
These types of orders can be classified into several types, each serving specific monitoring and control purposes within an organization’s financial management framework.
- Overhead Cost Orders: These are used to monitor and control overhead costs within an organization. With the right custom order management software, businesses can track expenses such as marketing campaigns, administrative activities, or non-direct costs by assigning specific overhead costs to these orders. This detailed tracking aids in budgeting and identifying opportunities for cost reduction.
- Investment Orders: Investment orders monitor the costs associated with capital investments, such as the acquisition of fixed assets. They help track capital expenditures throughout their lifecycle, from initial planning to completion, ensuring that the investment is accounted for and capitalized correctly in the company’s financial statements.
- Accrual Orders: These types of internal orders are designed to facilitate the accurate recording of accrued expenses and revenues. They bridge the gap between financial accounting and controlling by ensuring that period-related accruals are recorded systematically, enhancing the accuracy of financial reports.
- Orders with Revenues: These orders track both costs and revenues for specific activities. They’re particularly useful in scenarios where the company has not implemented a comprehensive sales and distribution component as part of its internal ordering system, allowing for the detailed monitoring of profitability for individual projects or services.
- Statistical Orders: Unlike other orders, statistical orders do not directly affect the financial accounting records. Instead, they’re used for internal reporting and analysis purposes. Costs are recorded against these orders for monitoring, but the designated cost centers bear the actual financial impact, providing a clear picture of internal expenditures without affecting the overall financial statements.
Each type of internal order plays a crucial role in the intricate process of financial management within an organization. It offers the flexibility and granularity needed to track and control costs effectively across various operations and projects.
Internal Orders vs. Customer Orders
When we typically think of orders for equipment or materials, we think about an external entity (the customer) ordering from a website or through a CSR and receiving the items directly. This is especially true with the growing volume of eCommerce sales. However, for many businesses—especially service businesses—internal orders come from employees for a job/customer. These orders, generated via custom order management software, have many of the same processes as an external order, but the reasoning behind them is different, and the KPIs are different.
Examples:
Orders for a Customer in a Service Business
This applies to a wide range of services, but a few good examples are cable and telecommunications, plumbing, and home security. In these cases, a customer account will be paying for the materials, but the order is coming through a service technician.
The internal order process is detailed below:
A technician will initially visit the site/home to determine what is needed. They will begin the order creation process to provide a quote to the customer. Ideally, the order can be submitted into an internal ordering system, such as our SCORE® Order Management Portal, pending approval so that it only has to be completed once. If the quote is accepted, the order is accepted, and the job is scheduled.
If the technician has everything they need on their service truck, the inventory can be deducted from the truck inventory, and the job can be completed. It’s important to think of the service truck as a mobile warehouse because, in this case, the truck’s inventory will need to be replenished. Otherwise, the order will be sent to the warehouse for them to pick and prepare.
 Internal Orders for Internal Infrastructure or Large Construction Jobs
Internal Orders for Internal Infrastructure or Large Construction Jobs
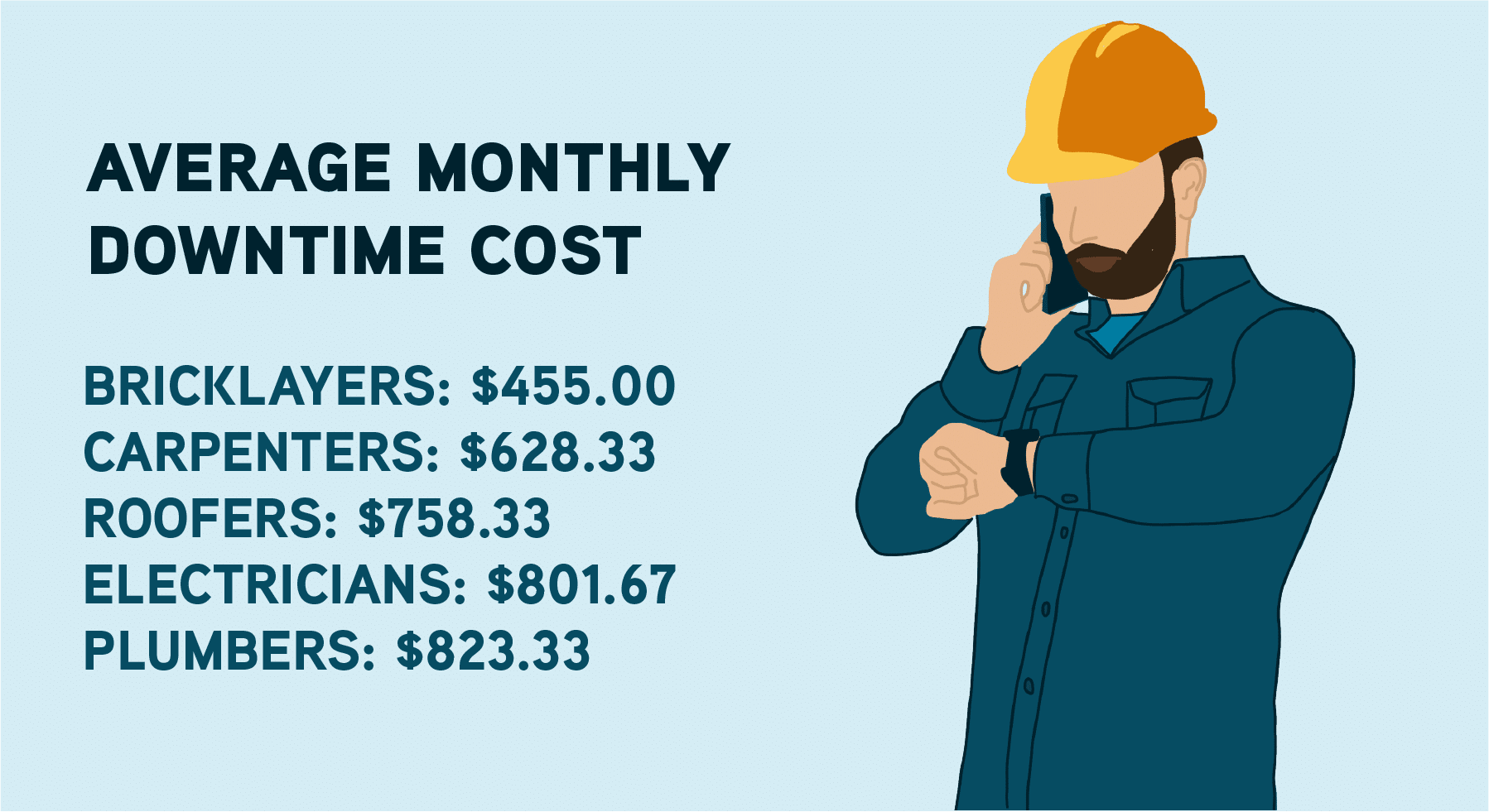
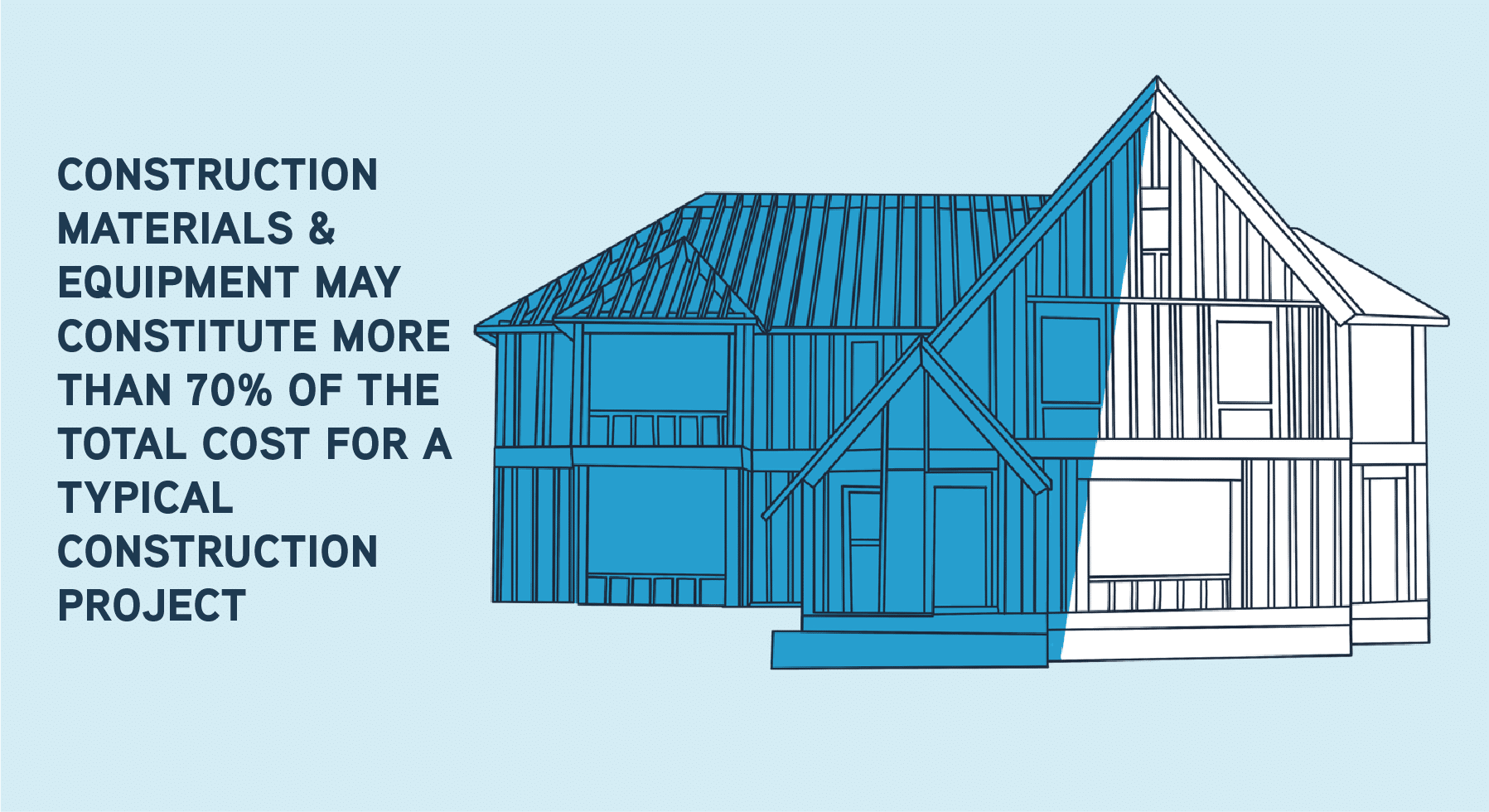
This often applies to utility companies and cable and telecommunications companies. Infrastructure and construction are longer processes, so job cost is a key metric that needs to be tracked. In these cases, orders come in from construction teams and are linked to a job. These orders can even come directly from a company’s architectural planning software.
With new construction and infrastructure, the timeline is much longer, and the orders are much larger. Ordering and scheduling are keys to success.
Ordering for Internal Use
Not as prominent, but just as important for monitoring costs and order management, ordering for internal use can apply to virtually any business. The internal order centers around internal purchases when one business unit or department orders supplies or new equipment. In these cases, the custom order management software is used for efficiently placing, preparing, and reconciling the items necessary for the order.
Key Considerations for Order Management Software
Order Templates
Many of the orders in a service business can be placed using an order form template to make the process quicker. For cable, this could be a new cable installation order consisting of a modem, set-top box, and cord kit. For electricians, this could be everything typically used in installing a breaker box.

Integrations
Ideally, the internal ordering system is integrated with the WMS and ERP. This gives all systems access to real-time data, projections, lead times, etc.
Additional integrations could include your:
- architectural planning application
- CRM for customer communication
- billing system (cable)
Approvals and Validations
One key benefit of internal orders is that you control both sides (ordering and fulfillment). This means you can validate orders to make the ordering process more efficient.
One example of this is what we call equipment family codes. When customers order something from an eCommerce site, they expect to receive that exact item. However, when technicians order something for a customer, they typically need something that works, but it does not need to be exact.
In the cable industry, this can be different modems. For most homes, many modems will work, so if the ordered modem is out of stock, it can be replaced with a different modem. This means a customer is not waiting for a specific product when another product works just as well.
Other internal order examples could be manager approvals of orders over a specific value or outside contractor approvals.
Have any questions about custom order management software? Need a customized internal ordering system? Call WDS today at 561-488-5540 or fill out our contact form to get in touch.



 Internal Orders for Internal Infrastructure or Large Construction Jobs
Internal Orders for Internal Infrastructure or Large Construction Jobs